Communication with EtherStat
Communication with the EtherStat server requires than any workstations where EtherSensor Agent is installed belong to the same local network. The EtherStat server uses encrypted TCP connection to collect information from workstations and then analysis it. The Agent generates unique UHIDs which identify workstations and sends them in the messages to the EtherStat server.
Transparent proxying without traffic marking with Microolap EtherSensor
In this mode, the Agent proxies transparently connections of applications which run on the user computer. If an application establishes a successful connection the Agent provides the Microolap EtherSensor server with information about the connection established by the specific application run by a specific network user.
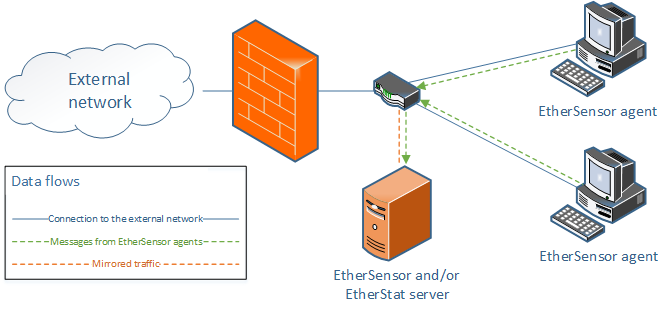
Figure 40. Transparent proxying without traffic marking
Thus, Microolap EtherSensor can reconstruct the message to completely identify the user who sent this message over any of the currently supported protocols (ICQ, MSN, MRA, IRC, XMPP, SMTP, POP3, LOTUS, HTTP, FTP, etc.).
The analyzed traffic must be turned readdressed to Microolap EtherSensor before any changes are made to connection parameters.
Examples:
▪To the proxy server.
▪To NAT.
▪To the network firewall.
Transparent proxying with HTTP traffic marking with Microolap EtherSensor
This operating mode of the Agent is only different from the non-marking mode in that the Agent modifies HTTP queries sent by applications on the client workstation by adding the X-Sensor-UID: <GUID> header to them where <GUID> is the unique user ID of the user of a specific computer within the local network. These actions are performed in strict accordance to the HTTP protocol without any violations of it.
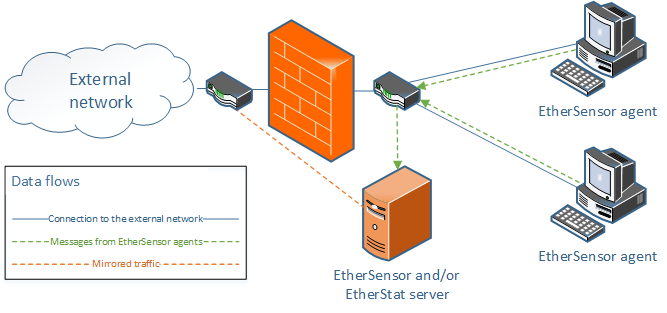
Figure 41. Proxying with traffic marking
The operating mode may be used when Microolap EtherSensor receives the traffic readdressed for analysis after connection parameters are modified. E.g. when connections pass through a proxy server, NAT or a network firewall.
In this case Microolap EtherSensor reconstructs the message to completely identify the network user who sent this message over the HTTP protocol.